androcg - Create Call Graph from APK¶
androcg can create files that can be read using graph visualization software, for example gephi.
Synopsis¶
usage: androcg.py [-h] [--output OUTPUT] [--show] [--verbose]
[--classname CLASSNAME] [--methodname METHODNAME]
[--descriptor DESCRIPTOR] [--accessflag ACCESSFLAG]
[--no-isolated]
APK
Create a call graph based on the dataof Analysis and export it into a graph
format.
positional arguments:
APK The APK to analyze
optional arguments:
-h, --help show this help message and exit
--output OUTPUT, -o OUTPUT
Filename of the output file, the extension is used to
decide which format to use (default callgraph.gml)
--show, -s instead of saving the graph, print it with mathplotlib
(you might not see anything!
--verbose, -v Print more output
--classname CLASSNAME
Regex to filter by classname
--methodname METHODNAME
Regex to filter by methodname
--descriptor DESCRIPTOR
Regex to filter by descriptor
--accessflag ACCESSFLAG
Regex to filter by accessflags
--no-isolated Do not store methods which has no xrefs
Examples¶
The call graph is constructed from the
Analysis object and then converted into a
networkx DiGraph.
Note that calls between methods are only added once. Thus, if a method calls
some other method multiple times, this is not saved.
The methods to construct the callgraph from can be filtered. It is highly suggested to do that, as call graphs can get very large:
Of course, you can export the call graph with androguard and filter it later.
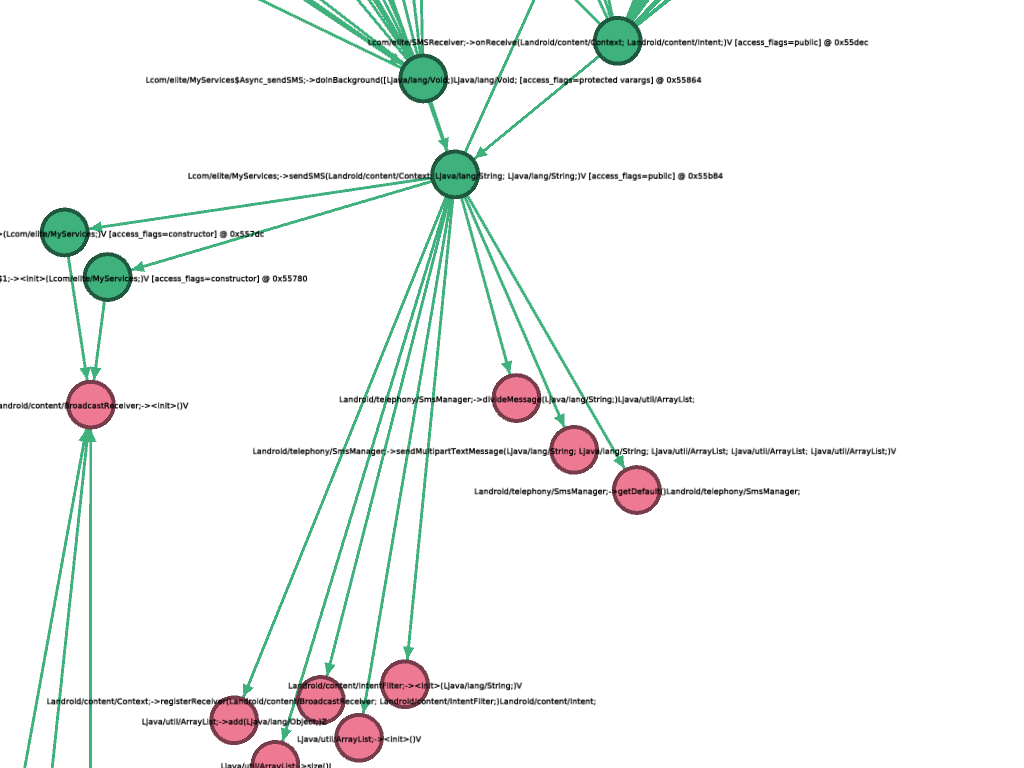
Here is an example of an already filtered graph, visualized in gephi. Each node has an attribute to indicate if it is an internal (defined somewhere in the DEXs) or external (might be an API, but definetly not defined in the DEXs) method. In this case all green nodes are internal and all red ones are external. You can see the calls of some SMS Trojan to the API methods to write SMS.